Implementing CyberSecurity into The Integrated Physical Security
- pjansta
- Jun 24, 2022
- 3 min read
Updated: Jun 27, 2022

This article will outline industry trends and how to effectively evaluate the project life cycle to develop suitable integrated physical security solutions whilst implementing cyber security best practices.
The convergence between physical and cyber is becoming ever so prominent. The cloud-based Access Control System and Video Surveillance are becoming cost-effective; hence users preferred options. For example, cloud storage for video, VMS, and SaaS.
The IT industry issues network hardening guides and video surveillance is catching up with some manufacturers issuing guides and vulnerabilities updates. Whilst manufacture specific, these guides are based around main cyber sec. themes.
· Best practices
· Strong passports management
· Firewalls
· Remote access
· VLAN’s architecture
· Cloud access
If the site and manufacturer-specific countermeasures are well documented and included in the security policy, they should remain effective.
1. Physical Security Systems and Hardening Guidelines
In addition to software, the components of installation typically include hardware devices,
such as:
· Cameras
· Encoders
· Networking products
· Storage systems
· Servers and client computers (physical or virtual machines)
· Mobile devices, smartphones
Including hardware devices to harden VMS installation is essential. For example, cameras often have default passwords. Some manufacturers publish these passwords online so that they’re easy for customers to find. Unfortunately, that means the passwords are also available to attackers.
Cyber Security researchers discover and report on vulnerabilities. They are often providing a summary of the vulnerabilities and their severity. Manufactures issue extensive vulnerabilities reports and guides and provide learning platforms. The emphasis is also on the supply chain and collaboration.
2. Dedicated or Converged Networks
Shall we use an existing network or deploy a new one? This is a critical choice when designing the solution. For example, access control is typically a low bandwidth application; the impact on shared and converged networks is much less of an issue compared to video systems.
Dedicated Networks
Often driven by the client’s policy, minimised cyber concerns, best practices, and more control. Dedicated networks will have a higher price tag attached.
Converged Networks
Converged networks share network resources between services like surveillance cameras, VoIP telephones, and general data traffic like email. This may be cost-effective when there are existing PoE ports to add surveillance equipment. Many networks were not designed to handle the demands of continuous video surveillance streaming. Local IT policy will retain control.
3. ISO Standards
The standards are becoming increasingly fractured between classical ICS, plus Industrial Internet of Things (IIoT) and Internet of Things (IoT), CCTV, BMS, and other monitoring devices. IT is equally becoming fractured with mobile (iOS and Android) diverging from IT plus outliers such as “wearables”.
The attack surface is exponentially increasing. The classic Purdue model (structural model for industrial control system (ICS) security, concerning physical processes, sensors, supervisory controls, operations, and logistics) is becoming more challenging for segmentation to protect ICS.
So, there is a need to think holistically whilst also understanding the specific security requirements for each technology domain, including those reliant upon third parties, I.e. SaaS, PaaS and IaaS, hosted services, etc. The UK NCSC is a good source of pragmatic guidance based upon what works, not what can be agreed upon, which is the essence of standards in this area.
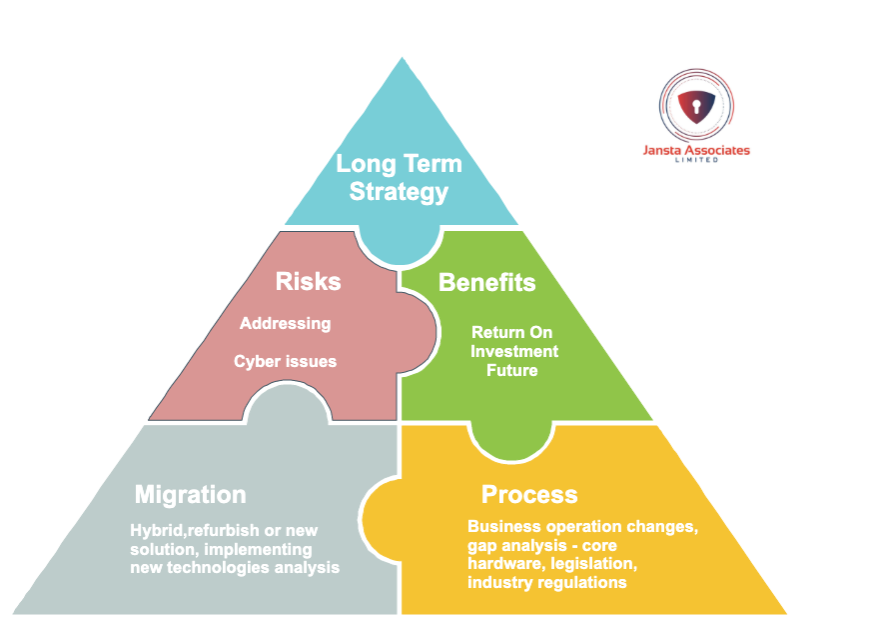
4. Project Life Cycle Evaluation
The deployment process is critical when developing a new or upgrading physical security solution.
Changes in how the business operates and risks associated with the security solution can’t be overlooked. A complete refurbishment is not always the most feasible option for an outdated security solution.
A dedicated network is often the preferred option in some countries stipulated by the legislation. The key to successful transformation is managing the stages and simplifying complex solutions.
Cybersecurity has become a vital issue, with published vulnerabilities, hacks, and botnets rising. Significant vulnerabilities have been reported in multiple manufacturers in the past few years.
Because of the severity of these incidents and their increasing frequency, users must understand the basics of cyber security for surveillance systems and how to protect against simple attacks at the very least.Cybersecurity issues have also contributed to government action against multiple manufacturers.




Again, Petr you have written something for everyone. I have no knowledge of IT & the security measures, systems or acronyms and abbreviations here. So have no comment.
However, I found section 3 thought provoking, and the reference to wearables (I don't) definately something to think about on a personal level.
I no longer use a removable memory card in my phone, and if used, it has no personal information or images, poertable not wearable, but loseable!